Cloud Storage for Business Receipts: Security Best Practices
Learn essential security practices for cloud storage of business receipts, including encryption, access controls, and employee training.

Did you know small businesses face 43% of cyberattacks, and 60% shut down within six months after one? Storing business receipts in the cloud can protect your financial data and ensure compliance with strict regulations like those from the SEC, FINRA, and IRS. But only if done securely.
Here’s how to keep your data safe:
- Enable Multi-Factor Authentication (MFA): Prevent unauthorized access.
- Encrypt Data: Protect receipts during storage and transfer.
- Regular Updates: Apply patches and monitor for threats.
- Train Employees: Reduce human errors in handling data.
- Backup Systems: Ensure quick recovery in case of data loss.
Choosing a Cloud Storage Provider
When picking a provider, prioritize these features:
- Encryption: Strong encryption for storage and transfer.
- Access Controls: Role-based permissions.
- Compliance: Certifications like ISO 27001 and IRS standards.
Quick Comparison of Top Providers
| Provider | Encryption | Key Features | Compliance Tools |
|---|---|---|---|
| Google Drive | 256-bit SSL/TLS (transfer), 128-bit AES (storage) | Admin controls, Workspace integration | Advanced admin tools |
| Dropbox | 256-bit AES (storage) | Dark web monitoring, secure sharing | Link expiration, sharing controls |
| OneDrive | Enterprise-grade security | Microsoft ecosystem integration | Compliance tools |
Actionable Tip: Start by enabling MFA, auditing access controls, and ensuring encryption is active. Regular audits and employee training can further strengthen your security framework.
5 Best Secure Cloud Storage & File Sharing Software in 2024
How to Choose a Cloud Storage Provider
Picking the right cloud storage provider is crucial for keeping your financial records safe and secure. Here’s a breakdown of the key factors to consider.
Security Features You Need
When it comes to protecting your financial data, look for these must-have features:
- Data Encryption: Check for strong encryption both during data transfer and while it’s stored.
- Access Control Systems: Opt for platforms that provide detailed, role-based access controls.
- Ransomware Protection: Ensure the provider includes tools to detect and prevent ransomware attacks.
| Security Feature | Why It Matters |
|---|---|
| Two-Factor Authentication | Prevents unauthorized access, even if passwords are stolen. |
| Data Loss Prevention | Helps identify and block potential data leaks. |
| Continuous Monitoring | Keeps an eye out for unusual or suspicious activities. |
| Automated Backup Systems | Allows for quick recovery in case of data loss. |
Staying Compliant with Financial Regulations
Your chosen cloud storage provider must align with financial regulations and data protection laws. Here’s what to look for:
- IRS Compliance: The provider should support digital record retention that meets IRS requirements for business documentation.
- Industry Standards: Verify certifications like ISO 27001:2013, ISO-27002, and ISO-27017, which highlight strong security measures.
Beyond meeting legal requirements, consider how providers implement these features to ensure your data stays secure.
Comparing Google Drive, Dropbox, and OneDrive
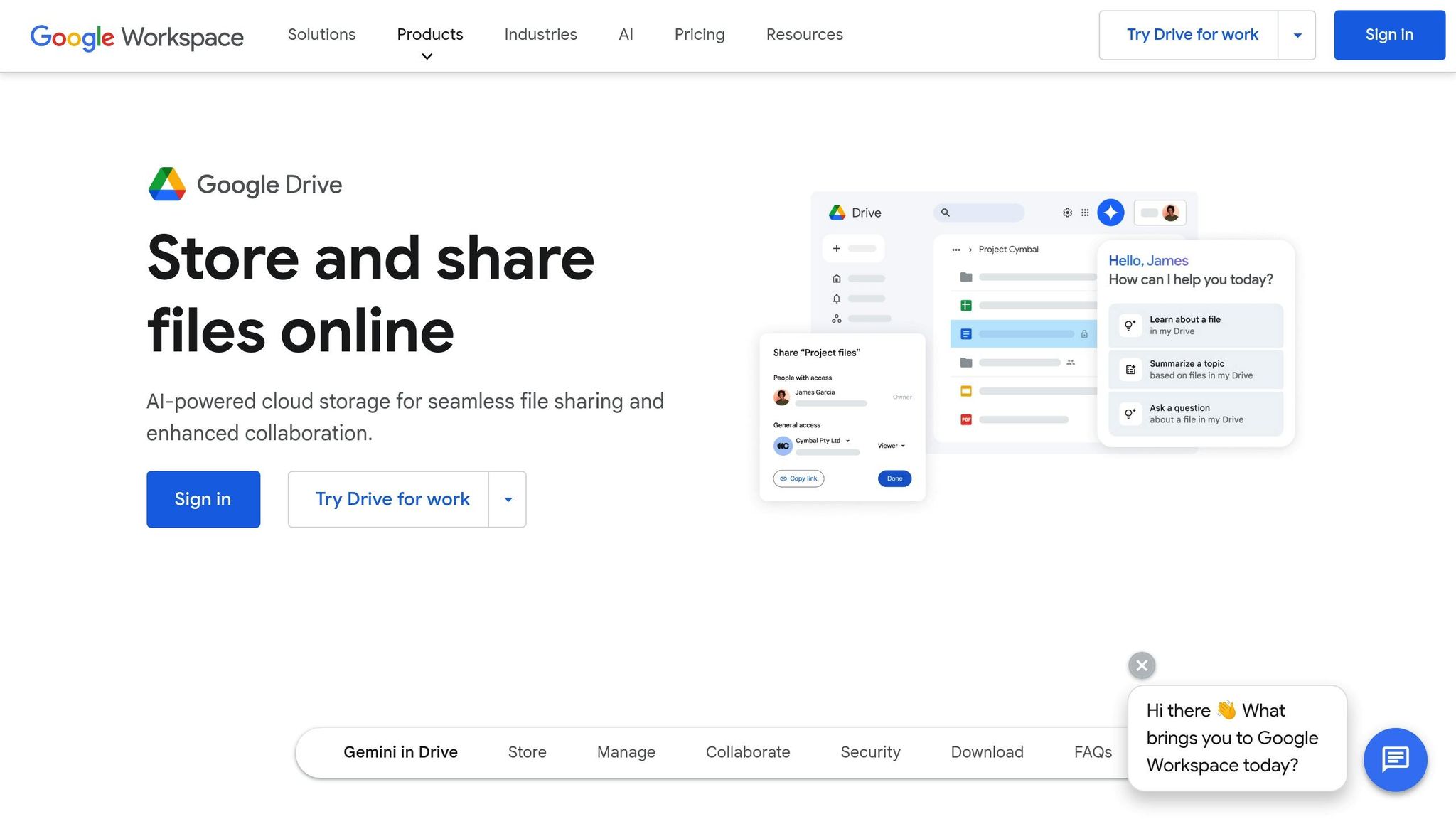
Let’s take a closer look at how the top three providers stack up in terms of security:
Google Drive:
- Protects data with 256-bit SSL/TLS encryption during transfer and 128-bit AES for storage.
- Works seamlessly with Google Workspace tools.
- Offers advanced admin controls through the Google Workspace security center.
Dropbox:
- Secures stored files with 256-bit AES encryption.
- Monitors the dark web for potential breaches.
- Features advanced sharing options, like password protection and link expiration.
OneDrive:
- Fully integrates with Microsoft’s ecosystem.
- Provides enterprise-level security features.
- Includes tools to help with compliance across various regulations.
A recent study showed that 62% of businesses rank data privacy and confidentiality as their top cloud security concern. This highlights the importance of choosing a provider that prioritizes robust security measures.
Setting Up Access Controls
Strong access controls are essential for keeping business receipts secure in the cloud. They help protect sensitive data and ensure compliance with regulations.
2-Factor Authentication Setup
In April 2024, Dropbox Business introduced mandatory 2FA, cutting unauthorized access by 60% and reducing phishing attempts by 25%.
Here’s how you can enable 2FA for your cloud storage:
- Go to your account's security settings.
- Turn on 2FA from your provider's dashboard.
- Choose between an authenticator app (recommended) or SMS verification.
- Download a trusted authenticator app like Google Authenticator or Authy. Scan the QR code provided to link your account.
- Save your recovery codes in a secure location for emergency access.
Once 2FA is set up, take the next step by defining role-based access to limit unnecessary data exposure.
User Access Levels
Role-based access ensures team members only see the data they need, following the Principle of Least Privilege. This minimizes security risks.
| Access Level | Permissions | Suitable For |
|---|---|---|
| Admin | Full system access | Finance managers, IT admins |
| Editor | Upload and modify data | Accounting staff, bookkeepers |
| Viewer | View-only access | Auditors, consultants |
| No Access | No data visibility | External contractors |
To manage access effectively:
- Review permissions every quarter with department heads.
- Log all access changes in a central system.
- Use HR tools to automate user provisioning.
- Revoke access immediately when an employee leaves.
Password Security Rules
Support these measures with strong password practices:
- Create passwords with at least 16 characters.
- Use a mix of uppercase and lowercase letters, numbers, and symbols.
- Avoid reusing passwords across services.
- Update passwords regularly and store them securely with a password manager.
Data Encryption Methods
Encryption is the backbone of secure cloud storage, especially for sensitive business receipts. A recent study found that 59% of IT professionals say managing encryption keys is a major challenge in their operations.
Complete Encryption Process
To ensure robust security, modern cloud storage uses both client-side and server-side encryption. This dual-layered approach strengthens data protection. Here's how it works:
| Encryption Type | When It Happens | Advantages | Key Responsibility |
|---|---|---|---|
| Client-Side | Before upload | Data encrypted directly on your device | You control the keys |
| Server-Side | After upload | Provider encrypts data automatically | Provider manages the keys |
| End-to-End | Entire process | Full protection from start to finish | Combines both methods |
Encryption Key Security
Managing encryption keys is critical. Over half (52%) of professionals report using at least five key management solutions across various environments. To safeguard your business receipts:
- Use Hardware Security Modules (HSMs): These provide secure, tamper-proof key storage.
- Deploy Key Management Systems (KMS): Automate the creation, rotation, and deletion of keys.
- Separate Keys by Category: Assign unique keys for different types of receipts to limit exposure.
- Store Keys Separately: Never keep encryption keys in the same location as the encrypted data.
"One area we caution our healthcare clients to watch out for is the storage and use of encryption keys. They often store the keys in the same location as the data itself." - Cortney Thompson, Chief Information Officer at Lunavi
Data Security: Storage vs Transfer
Encryption keys are essential for access control, but data also needs protection whether it's stored or being transferred. Alarmingly, ransomware can encrypt nearly 100,000 files (53.93GB) in just 42 minutes and 52 seconds.
Here’s how to ensure strong protection:
| Data State | Encryption Method | Purpose |
|---|---|---|
| At Rest | AES-256 | Protects stored receipts |
| In Transit | TLS 1.3 | Secures data transfers |
| Backup | Symmetric encryption | Safeguards archived copies |
For stored receipts, symmetric encryption (like AES) is faster and efficient. During transfers, asymmetric methods (like RSA) offer stronger security. Combining these methods creates a more layered and secure defense.
Security Audit Process
Audits go beyond basic encryption and access controls, ensuring these measures work as expected.
Access Log Review
Thorough log reviews can enhance threat detection by up to 40%. Focus on these key log types:
| Log Type | What to Monitor | Warning Signs |
|---|---|---|
| Authentication Logs | Login attempts and timing | Multiple failed logins, access during odd hours |
| Data Access Logs | File operations and user actions | Bulk downloads, unusual access patterns |
| System Logs | Server and application activity | Traffic spikes, resource irregularities |
Using a SIEM (Security Information and Event Management) system can simplify log collection and automate reporting. After analyzing logs, conduct routine tests to ensure security measures remain effective.
Security Testing Schedule
Consider this structured approach for regular security checks:
- Weekly Tests: Perform vulnerability scans every week to catch potential issues early.
- Monthly Assessments: Run targeted penetration tests on critical systems after updates.
- Quarterly Reviews: Assess access controls and update security policies. With 55% of employees using personal devices for work, keeping policies current is crucial.
After each test, address vulnerabilities immediately to minimize risks.
Security Updates
"Clarify the scope of your cloud security audit by explicitly defining the boundaries of your responsibility versus the cloud provider's".
Stay ahead of threats with these proactive measures:
- Use automated patching systems to address vulnerabilities quickly.
- Update your incident response plans annually.
- Schedule independent security assessments twice a year.
- Keep an up-to-date inventory of all endpoint devices.
Regular updates and maintenance are essential to protect your systems and data.
ReceiptsAI Security Features
ReceiptsAI takes security seriously, combining AI-powered receipt management with strong protective measures to keep financial documents safe. With over 10,000 documents processed for more than 300 small businesses, the platform demonstrates its ability to securely handle receipt management.
AI Receipt Processing
ReceiptsAI's system uses AI to extract data while maintaining strict security standards. Key security measures include:
| Security Measure | Implementation | Benefit |
|---|---|---|
| Data Validation | Advanced OCR with accuracy checks | Prevents tampering or data manipulation |
| Access Control | Customizable processing limits | Allows users to control data access |
| Secure Storage | US-based servers with compliance focus | Ensures safe and compliant data handling |
To further secure email traffic, ReceiptsAI employs DKIM, SPF, and DMARC standards.
Bank-Grade Security System
ReceiptsAI adopts security measures that align with banking industry standards, ensuring your data is well-protected. The platform boasts 99.62% uptime and includes:
- SSL encryption for all network connections
- Enterprise-grade encryption for stored data
- Secure partnerships with thoroughly vetted third-party providers
"At Receipts AI, your privacy and the protection of your data is our top priority." – Receipts AI
ReceiptsAI complies with GDPR regulations and uses Stripe for payment processing, meaning no credit card details are stored on its servers.
The platform's flexible design allows it to adjust its security features based on varying business needs.
Business Plan Options
ReceiptsAI offers three plans, each with built-in security measures:
| Plan | Cost/Month | Pages | Security Features |
|---|---|---|---|
| Free Tier | $0 | 30 | Basic SSL encryption, secure storage |
| Starter | $12 | 100 | Advanced encryption, data export options |
| Premium | $29 | 500 | Priority security support, extra protection |
All plans include SSL encryption and secure US-based storage, ensuring consistent protection.
"I used to spend hours manually entering receipts into spreadsheets. Now I use ReceiptsAI to do it automatically. It's a lifesaver!" - Norma W., Real Estate Company President
Summary and Next Steps
Cloud security breaches are hitting small businesses hard, with an average cost of $180,000 per incident in 2025. To safeguard your receipts and other sensitive data, follow this practical security plan:
| Priority | Action Item | Timeline |
|---|---|---|
| Critical | Enable MFA & Access Controls | 24 hours |
| High | Set Up Data Encryption | 1 week |
| Medium | Document Security Policies | 2 weeks |
| Ongoing | Conduct Regular Audits | Quarterly |
Start by assessing your current cloud storage setup to identify weak points.
"Choose your cloud provider carefully and consider security according to your industry, company size, actual business need, and local data privacy laws." - Tresorit Team
Here’s a breakdown of your next steps:
Immediate Actions
- Enable two-factor authentication (2FA) for all cloud accounts.
- Audit user access permissions and align them with job roles.
- Verify that encryption is active for both stored and transmitted data.
- Plan quarterly training sessions to boost security awareness.
Building a Stronger Security Framework
After addressing immediate priorities, focus on these essential measures:
- Set up automated backups stored in a separate geographic location.
- Install monitoring systems to detect unusual access patterns.
- Configure firewalls tailored to your cloud environment.
- Create and maintain detailed documentation of your cloud security policies.
Human error accounts for 95% of cloud security failures. With over 94% of small businesses relying on cloud services in 2025, staying vigilant is critical.
To stay ahead of threats, make continuous access monitoring a standard practice and schedule security audits every three months. This proactive approach can help you catch vulnerabilities before they turn into costly problems.





